Describe the Mitigation Strategy for Controlling Risk
In case if the risk becomes an outcome the we have contingency plan to reduce the impact of the risk. Businesses take some type of action to address a perceived risk and regulate their exposure.

Strategic Risk Management Synergy Consulting
In mitigation we take preventive measures to reduce the likelihood of the risk or to reduce the impact of the risk in case it occurs.

. The key to reducing your risk lies in the strength of one or more of the mitigating controls for your business continuity program. Describe the purposes and benefits of each one the challenges involved in creating each one and. Here are 6 top strategies for mitigating cybersecurity incidents across your IT ecosystem.
This strategy can be appropriate under the following scenarios. The first step in a cybersecurity risk mitigation strategy should be to conduct a cybersecurity risk assessment which can help uncover potential gaps in your organizations security controls. Transferring to another party.
Assume and accept risk. In this case we transfer the risk to third party who. The project manager should deal with the risk owner in order to decide together which strategy to implement to resolve the risk.
Risk limitation usually employs some risk acceptance and some risk. Appropriate risk mitigation involves first identifying potential risks to a projectlike team turnover product failure or scope creepand then planning for the risk by implementing strategies to help lessen or halt the risk. Risk mitigation is the strategy of preparing for and lessening the impact of threats a business may face.
With multiple strategies available risk managers have plenty of tools to deal with business risks threats and vulnerabilities in the enterprise. When the project members talk about accepting the risk they collaborate with each other while. A risk mitigation strategy has a medium cost and a high return.
Mitigation begins with the early detection of an attack in progress and the organization s ability to respond quickly efficiently and effectively. Instead of countering the attack mitigation control strategy lightens the severity of successful attack. Mitigation techniques aim to lower the potential impact of a risk and decrease the likelihood of the risk event from occurring.
The mitigation strategy is the control approach that attempts to reduce the impact of exploited vulnerabilities through planning and preparation. For each identified risk based on priority a mitigation plan or strategy is created. While different strategies may be used for various risks.
Describe the challenges and benefits of implementing a cyber security risk mitigation strategy for a real or fictional company. Mitigation This strategy is the control approach that attempts to reduce by means of planning and preparation the damage caused by a realized incident or disaster. Five risk mitigation strategies with examples.
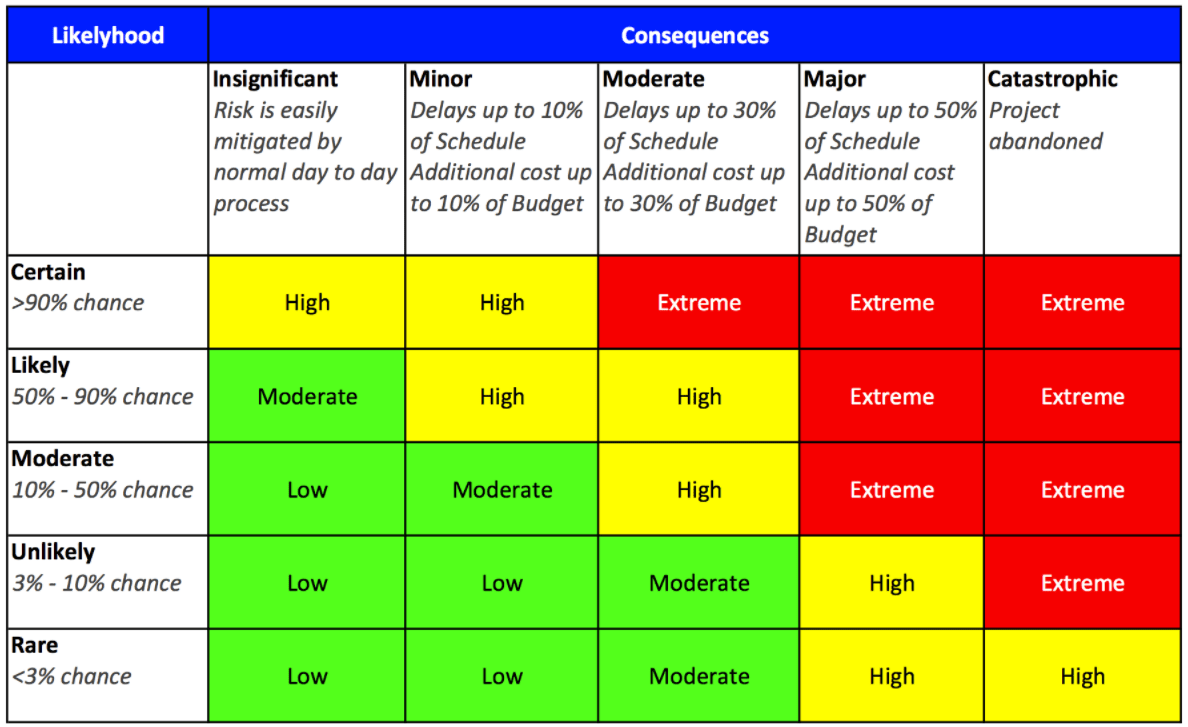
There are four primary mitigation techniques that may be used and. High impact high probability risk. To mitigate risk is to take steps to minimise the impact of a negative event occurring through careful planning.
Here are the 4 most common risk mitigation strategies. Obviously every strategy to respond to the risk is useless if it is not monitored in its success or failure. This approach includes three types of plans.
Each of these controls plays a role in the success of the program. Defense risk control strategy occurs when a department or business tries to avoid the risk altogether by preventing the vulnerability that has been identified from being exploited. Conduct a risk assessment to determine vulnerabilities.
If you cant avoid the risk altogether or you cant afford to accept it entirely then mitigation is the next logical step. Avoiding the risk is a strategy where the team members come up with ways in which they can avoid the. An organization that cant afford much money to avoid risks can use this strategy to at least reduce the impact of the attack or risk.
Businesses will outline a risk mitigation plan for potential situations that are either inevitable to happen or cannot be entirely avoided. Precautions like insurance are common methods of risk mitigation. The following strategies can be used in risk mitigation planning and monitoring.
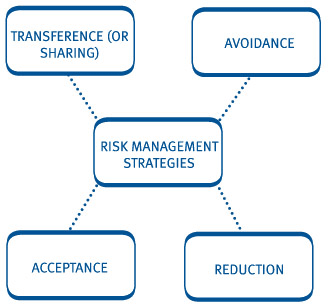
Risk mitigation is central to business continuity. With its high return risk mitigation could be a good strategy here if risk avoidance is unaffordable. Risk Mitigation Strategies Accepting the risk.
REDUCE RISK strategy The most common mitigation strategy is risk limitation eg. An organization that cant afford much money to avoid risks can use this strategy to at least reduce the impact of the attack or risk. Risk avoidance involves an alternative strategy with a higher cost that would result in a higher probability of success.
If one or more are. The risk will not be completely be removed but its impact andor likelihood will be reduced. It is the act of taking steps to reduce the extent of exposure to a risk andor the likelihood of its occurrence.
For example a common risk avoidance technique uses existing proven methodologies instead of adopting new ones as. Instead of countering the attack mitigation control strategy lightens the severity of successful attack. Risk mitigation strategies are an important part of an overall enterprise risk management program and its associated risk mitigation planning activities.

Pengertian Risk Management Dari Berbagai Sumber Kantor Akuntan Publik Suryanto Ak M Si Ca Cpa Csep

The Cfo And Strategic Risk Management Strategic Finance
4 Great Risk Mitigation Strategies For Your Business Monday Com Blog
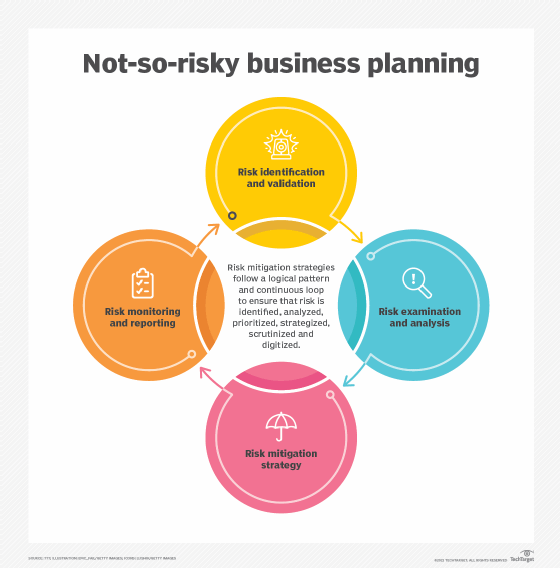
7 Risk Mitigation Strategies To Protect Business Operations
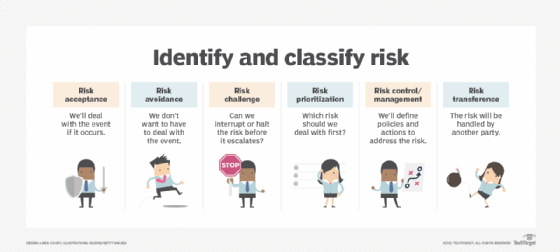
7 Risk Mitigation Strategies To Protect Business Operations

Cara Efektif Membuat Penilaian Risiko Risk Assessment Proxsisgroup
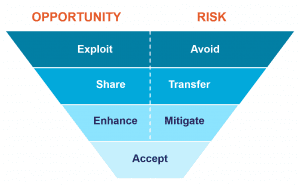
The Risk Management Process 4 Essential Steps M P

Four Types Of Risk Mitigation And Bcm Governance Risk And Compliance
Risk Mitigation Planning Acqnotes

Covid 19 And The Need For Robust Risk Control Strategies Can Ich Q9 Help Ivt

How To Perform An It Cyber Security Risk Assessment Step By Step Guide Cyber Security Risk Management Strategies Assessment

Enterprise Risk Management Erm
4 Great Risk Mitigation Strategies For Your Business Monday Com Blog

10 Types Of Risk Management Strategies To Follow In 2021 Auditboard

10 Types Of Risk Management Strategies To Follow In 2021 Auditboard

Risk Management Strategy An Overview Sciencedirect Topics
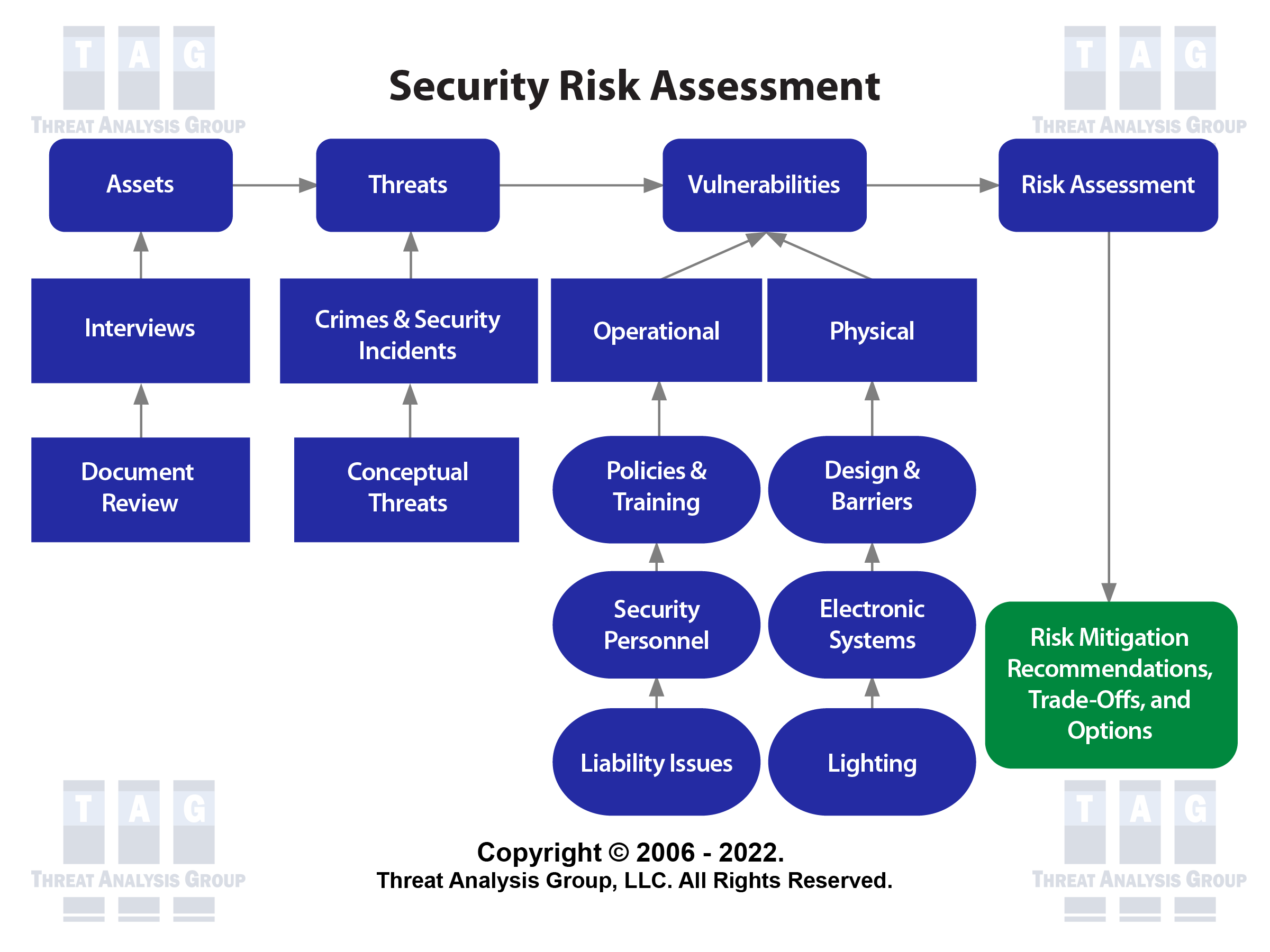
Security Risk Management Threat Analysis Group

Risk Management Strategies And The Role Of Senior Managers Grin
Comments
Post a Comment